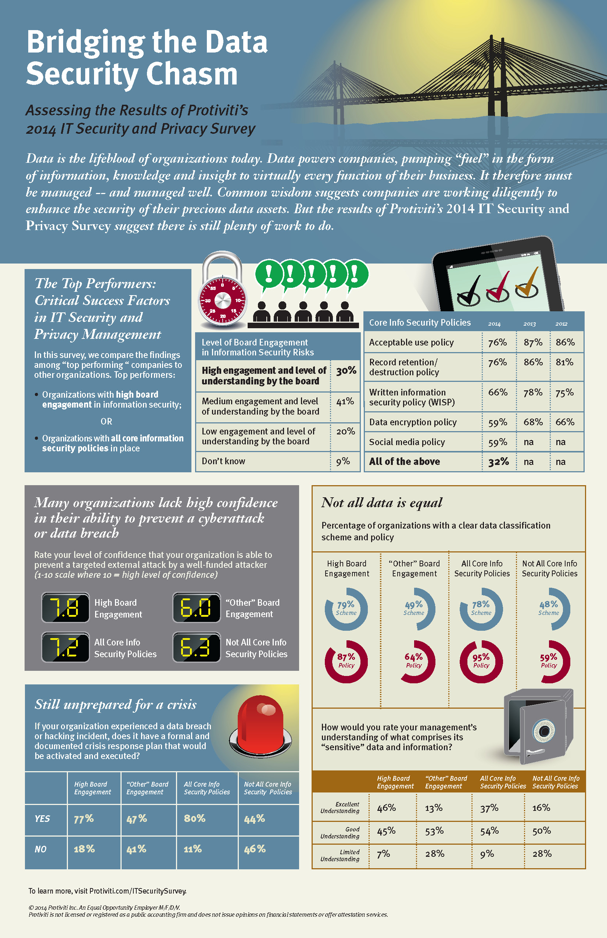
If data isn’t the lifeblood of an organization, it is, without question, a critical component in its success. Analogous to the role of water in a hydroelectric plant, data powers an organization, pumping “fuel”–through information, knowledge and insights–to virtually every company function. It, therefore, must be managed–and managed well. With the recent plethora of cyber attacks and data breaches, prevailing wisdom suggests companies are working diligently to “get their houses in order,” but findings from Protiviti’s “2014 IT Security and Privacy Survey” suggest otherwise.
There are numerous data management and security policies organizations should have in place to help prevent data loss (for example, information security, passwords, user access, incident response, etc.). Remarkably, this year’s survey results show across-the-board decreases in the number of organizations that have these policies in place. Most of these policies are required in some form in order to comply with various government and industry regulations. Thus, organizations potentially face significant liability, along with security risks, by not having these policies in place.
Our survey findings also indicate that there is an increase in the number of organizations that lack a data classification scheme. A look at these findings reveals significant gaps between top-performing organizations and other companies. Some organizations may lack definitions of their sensitive data and, consequently, fail to make meaningful progress in formalizing a scheme and policy. It’s important to note, though, that these definitions do not need to be perfected in order to begin categorizing data effectively.
Our survey findings also indicate that there is an increase in the number of organizations that lack a data classification scheme. A look at these findings reveals significant gaps between top-performing organizations and other companies. Some organizations may lack definitions of their sensitive data and, consequently, fail to make meaningful progress in formalizing a scheme and policy. It’s important to note, though, that these definitions do not need to be perfected in order to begin categorizing data effectively.
Effective data classification, without question, is difficult to achieve. Companies should strive to simplify their approach where possible, which will enable greater progress and success with these efforts. There are two data classification approaches every company should employ:
1. A data classification scheme: The groups or categories under which data is classified (for example, personally identifiable information; sensitive, health and confidential identifiable information; and non-sensitive and public information).
2. A data classification policy: The guidelines dictating how, when and where the organization–including, but not limited to, all employees, functions and third parties working on behalf of the organization–classifies, manages and secures its data.
In our study, we continue to see a relatively small percentage of organizations that have a detailed data classification system in place, which involves stratifying the importance of data types and applying appropriate retention periods to each type based on regulatory and legal requirements, as well as industry or company-defined standards. Such a system becomes more critical every day due to the growing volumes of data organizations are accumulating. An essential practice in effective data management and security is a comprehensive classification system that provides a clear understanding of how the organization is managing all types of data–whether sensitive, confidential or public.
The survey also uncovered that the percentage of organizations that retain all data and records without a defined destruction date has nearly doubled. Retaining all data and records without a defined date to discard and destroy is not only inefficient and costly but opens the organization to significant security risk and liability. The greatest effects of large-scale, high-impact breaches are felt in organizations that hold on to large volumes of data that they no longer need. Put simply, “If you don’t need it, don’t store it.”
Similar to last year’s findings, in one out of four organizations, management is viewed to have limited or no understanding of its sensitive data and information. Given the risks and liabilities this information poses if not managed properly, these findings continue to be surprising. There are striking differences in the findings among top-performing organizations (for example, high levels of board engagement in information security risks and all core information security policies in place). Clearly, these best practices are driving a much greater understanding of the organization’s sensitive data and information.
Cal Slemp is a managing director with Protiviti and currently leads the firm’s security and privacy solutions consulting business globally. For more information on Protiviti’s “2014 IT Security and Privacy Survey,” visit www.protiviti.com/itsecuritysurvey.