
Image by: maxarion, ©2016 Getty Images
If you didn’t already know, there is a new sheriff in town within the corporate structure, and it’s the chief information security officer (CISO). If you need proof, look no further than the White House, with its recent Cybersecurity National Action Plan that includes a $3.1 billion Information Technology Modernization Fund and the newly minted position of the first federal chief information security officer. Furthermore, according to Gartner, the number of large enterprises reporting to their board of directors on cybersecurity and technology risk at least once a year will rise from today’s 40% to 100% by 2020. One thing is certain: Security problems are emphatically business problems.
What’s changing?
In the pursuit of the digital business, we are witnessing an evolution of how we view cybersecurity within the larger digital ecosystem and the emergence of the “business unit information technology (IT).”
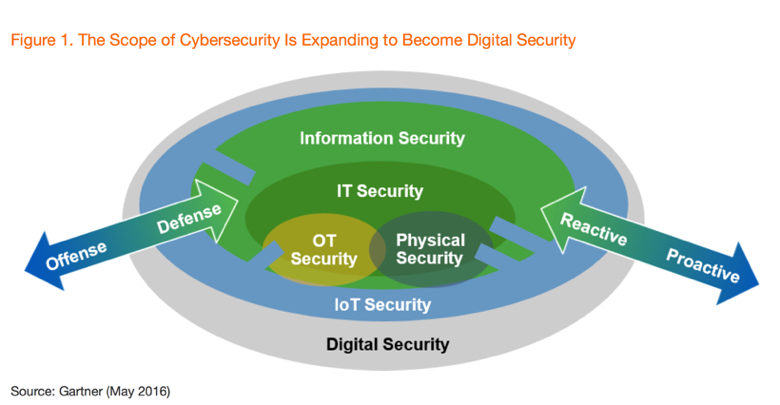
In fact, Gartner Analysts Paul Proctor and Ray Wagner in their recent report, “Cybersecurity at the Speed of Digital Business,” conclude that “security officers will work more like intelligence officers and trusted advisors, as citizen and business unit IT becomes the dominant model.” They go on to predict that “by 2020, 60% of digital businesses will suffer major service failures due to the inability of IT security teams to manage digital risk.” Thus, it’s no surprise to see that the investment of rapid detection and response approaches will double in enterprise information security budgets in the next four years.
Follow best practices
As the numbers pointedly show, it’s not about if you have a security incident but when. The real difference will be if you have the processes, polices, and expertise on hand to face such occurrences in the quickest fashion with the least amount of damage to the brand. So, how can organizations prepare for the inevitable? To outline some core best practices, I sat down with Scott Gordon, chief operating officer of FinalCode, a California-based file security software company that provides file security management, file encryption, and a file-based enterprise digital rights management platform. He suggests the following three best practices to consider:
1. Create a lightweight risk management framework.
Frame organizational risk and security controls around three areas of the business: key aspects of the business that have to be available, key aspects of the business that have compliance/regulatory liabilities, and the key aspects of the business that enable growth or productivity—underlined by the business risk, which is the probability of an occurrence multiplied by the cost of a potential incident. Highly regarded frameworks for risk management and IT governance include the National Institute of Standards and Technology SP 800-39 and Control Objectives for Information and Related Technology (COBIT), which can be adapted to the business.
2. Assume you are going to have a security incident, and map out the processes and expertise required for the high probability of an incident.
Involve your legal counsel, your communications teams (whether internal or outside agencies), and forensic and investigation experts to review the most probable areas for an incident and the processes should an incident occur, all to be documented in a handbook that’s revised and reviewed.
3. Tailor a security awareness program for your audience.
Build a specific awareness program for your board of directors, business executives, and users. This should not just include operational practices but also hit on business ethics.
Why the CISO is turning business heads
Over the last 10 years, the CISO has steadily been making a case for their seat at the table. With the call from board of directors to be briefed on security and IT risk more often instead of less, it seems the CISO’s time has arrived, but why now? Gordon says, “Education. They are explaining their capabilities and achievements in business terms (i.e., how they are achieving their targets for implementation, reducing response time to security problems or issues with different lines of business, or how they have saved money in their individual programs), showing operational value. They are relaying their programs in terms or metrics that business people can understand.”
Moving away from overly technical language and technology-focused milestones creates separation from the idea that security is an IT problem—historically, a popularly held belief by many senior-level business executives—when it’s, in fact, a business problem. In addition, the prevalence of shadow IT and the shifting business-centric model has carved out a role for security professionals to become trusted advisors and educators to these lines of business. However, there is still work to do. While boards might understand they need to care about security risk, they don’t always know what they should ask in terms of the business metrics they care most about. No, that is left to security professionals. CISOs must constantly be aware of operational value, strategic goals, and potential business risk in opposition of those goals while directly aligning the security controls necessary to achieving business objectives. It might be a thankless job indeed.
Allison Lloyd serves as the editor of DOCUMENT Strategy Media. She delivers thought leadership on strategic and plan-based solutions for managing the entire document, communication and information process. Follow her on Twitter @AllisonYLloyd.
















