
©2016 Getty Images
We know there are risks of data loss and data breaches by external hackers and fraudsters. We see this reported daily. While this is of concern, it is the internal threat of theft by staff or ex-staff that is considered to be the greater risk by many organizations. It is internal staff, with malicious or financial motivations, that will always be in a better position to copy, remove or even destroy vital business information–often undetected–until it is too late.
Another point of data leakage is through poor disposal practices. This includes everything from deskside recycle bins for paper-based information, removal and disposal of hard drives from personal computers and servers, USB devices and even back-up tapes and CDs. While loss of data in this way could be considered staff negligence, it also points to a lack of corporate policy regarding proper and defensible disposal of storage media and the need to monitor or audit disposal processes.
AIIM research from the Industry Watch Report titled “Data Privacy – living by new rules” shows that more than 50% of respondents feel the greatest threat of data loss or theft comes from internal resources.
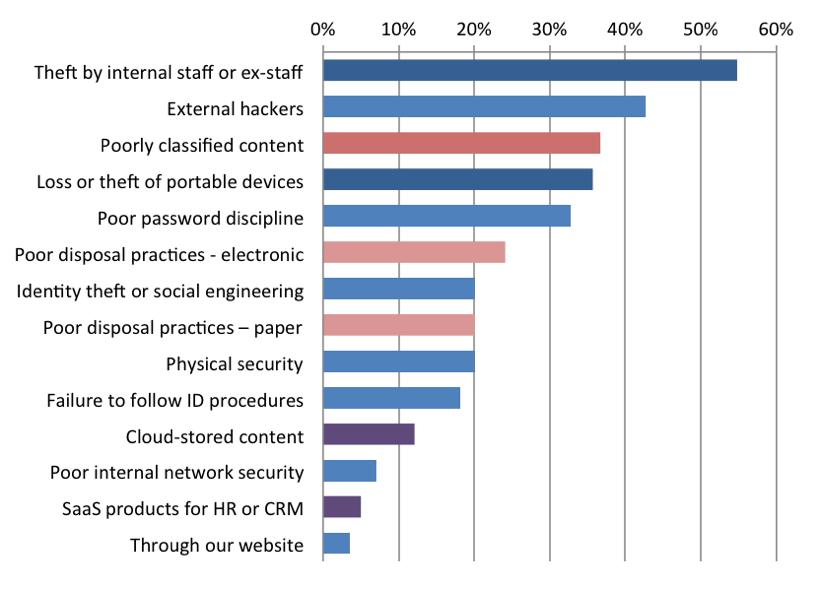
A recent study by AIIM asks respondents where they feel the organization is most vulnerable to data theft, loss or exposure.
Source: AIIM, Jan. 2016.
Consider this
There are many reasons an employee or contractor may copy and remove vital information from within the secure confines of the information ecosystem. For example, there may be a need to complete tasks related to a project, and the most expeditious way to do so includes taking work home or on the road while on business travel. For those honest, rule-abiding employees, there are technologies in place to support this work scenario. So much for the unsuspecting risk taker, what about the malicious person?
What to think about
First and foremost, there must be governance education regarding information practices and technology use. Who is authorized to do what? How does one adhere to corporate policies? What tools are to be used to manage corporate information? What are the consequences for non-compliance?
Most important is how the environment is monitored to detect potential loss. This could include use of an email management system that monitors incoming and outgoing email, URL restrictions to prevent access to personal email and cloud storage services from corporate equipment and network monitoring and repository audits to identify who is attempting to access various information data elements.
In my view
Even when policies are in place, policy alone will not deter malicious intent and activity. There must be a level of control in place to monitor and detect potential data loss from both external and internal threats. There must be regular review cycles with employees and contractors on corporate information management policies, with an acknowledgement and acceptance to adhere to them. There must be a mechanism in place to monitor the information ecosystem as a preemptive security measure to ensure internal threats are as unsuccessful as external threats.
Information security is the responsibility of all employees. If the right measures are taken, there is a greater chance of saying, "I know where my information is, and it is secure," rather than "Where has all the data gone?"
Bob Larrivee is vice president of market intelligence at at AIIM and an internationally recognized subject matter expert and thought leader with over 30 years of experience in the fields of information and process management. He is an avid techie with a focus on process improvement and the application of advanced technologies to enhance and automate business operations. Follow him on Twitter @BobLarrivee.
















