Image by: Pixsooz, ©2016 Getty Images
Attitudes and motivations toward protecting this data are wide-ranging, as are the gaps resulting from increased volumes of content and where it is stored, such as laptops, mobile devices and cloud. Many organizations lack a comprehensive information governance regime to deal appropriately with the changing requirements that technology and content sources introduce to an organization.
AIIM research from the Industry Watch Report titled “Data Privacy – living by new rules” shows that 24% of respondents feel that their senior managers do not take the risks of data privacy breaches seriously. Thirteen percent believe that operational considerations override compliance.
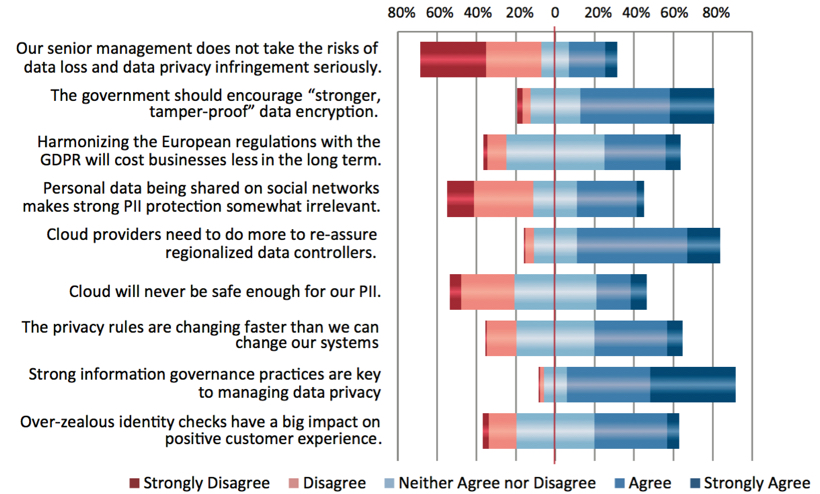
AIIM's latest research report shows respondents' feelings on statements regarding data privacy and information security.
AIIM Industry Watch Report “Data Privacy – living by new rules,” January, 2016.
Consider this
In order to appropriately protect sensitive information or, for that matter, information of any type, it must first be identified and classified correctly. Many organizations suffer from information chaos, aware that misallocated, redundant content resides within their repositories. Accidental exposure of this content—especially if it involves employee or client data—is often raised as a concern. The key, and challenge, in all of this is to identify the information and content you have, correctly classify and tag it, remove any redundant, obsolete and trivial (ROT) content and add appropriate security controls to protect your information assets.
What to think about
Conduct initial and periodic information audits. Document personally identifiable information (PII) you hold on employees, customers or citizens and whether it constitutes sensitive personal data. Ensure that your information governance policies include security elements related to PII, and present the appropriate use of laptops, USB sticks and mobile devices in relation to PII. Something as simple as a privacy screen filter on a laptop could mean the difference between secure information and future unauthorized access using your credentials.
Conduct a risk assessment related to PII and the impact should it be lost or exposed. Create an awareness among senior management as to the potential consequences of a breach, including those involving internal staff, and educate the user community on the importance of security, governance policies and procedures and the related technology used to ensure information protection.
In my view
Information security and data privacy are practice areas that should include the entire enterprise, not just information technology (IT) or a select part of the organization. It is a team effort to ensure security is maintained. Much in the way that law enforcement promotes citizen engagement by encouraging the reporting of unusual activity, business organizations should feel compelled to train and engage their corporate citizens in security practices and the reporting of unusual activities related to PII.
Information is a corporate asset that must be protected—by all. The time is now for senior management to step up and to be proactive in designing an information security framework before it is too late.
Bob Larrivee is vice president of market intelligence at at AIIM and an internationally recognized subject matter expert and thought leader with over 30 years of experience in the fields of information and process management. He is an avid techie with a focus on process improvement and the application of advanced technologies to enhance and automate business operations. Follow him on Twitter @BobLarrivee.