Enterprise Content Management (ECM) applications form the backbone of many vital digital document processes in businesses today. These systems serve as a hub, potentially thousands of users accessing repositories daily, seeking to view and interact with an organization's most secure and valuable digital assets. The magnitude of user activity generates an immense quantity of document transactions. In light of this, comprehending the nature of user interactions with the repository content and their usage patterns becomes crucial. This understanding paves the way for effective content management, improved user experience, and enhanced security measures, thereby contributing to an organization's overall operational efficiency and success.
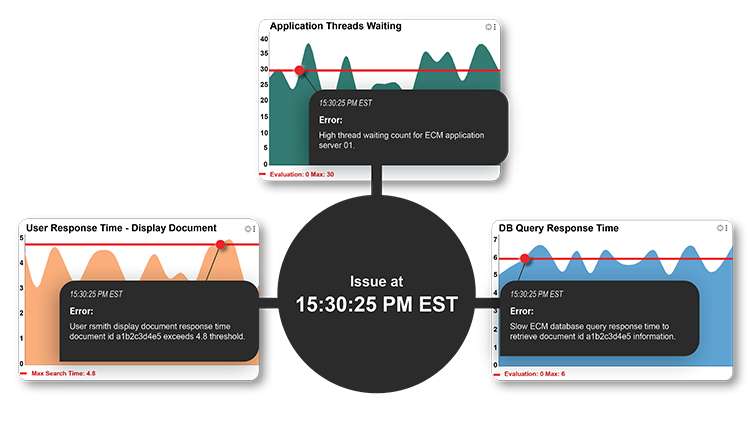
For example, in Figure 1 above, an issue occurs at 15:30:25 EST. This organization has decided that a search above 4.8 seconds for user response time warrants notifying appropriate personnel. This instance is a snapshot, along with the data from the same time for the repository and infrastructure. This type of user activity insight (correlated with ECM platform fault domain identification) allows for quicker issue detection and resolution.
Given the context outlined, the importance of effectively managing ECM user activity cannot be overstated. There are four primary reasons for this emphasis.
1. Know Your Business Performance and Plan Ahead
Users dealing with objectively slow content retrieval must be equipped to perform optimally. Whether they are processing payments, loan documents, accessing design specifications or viewing lab reports, understanding and managing the time of these transactions is critical for business. In addition, user response time impacts Service Level Agreements (SLAs); knowing real user response time with document context allows organizations to identify and resolve service level issues.
Along with document responsiveness for users, knowing the scope of user activity allows proper planning for growth. Without insight into transaction volumes or repository usage, attempting to plan capacity needs could result in problems that may have otherwise been prevented. Knowing your current performance footprint is necessary when considering ECM workload rebalancing using on-premises, cloud hypervisors, private cloud or hybrid architecture options. Otherwise, even ‘lift and shift’ approaches, commonly used for speed and simplicity, will not be effective.
2. Dramatically Reduce Mean Time to Detection (MTTD) With Correlated ECM Platform Information
Proper insight into your ECM system and user activity allows for quicker identification of issues. The ability to have a snapshot of the ECM user, repository and infrastructure when a threshold is passed — dramatically reduces the time of an investigation.

For example, in Figure 1 above, an issue occurs at 15:30:25 EST. This organization has decided that a search above 4.8 seconds for user response time warrants notifying appropriate personnel. This instance is a snapshot, along with the data from the same time for the repository and infrastructure. This type of user activity insight (correlated with ECM platform fault domain identification) allows for quicker issue detection and resolution.
3. Insider Threat Detection for Content
One of the most significant security challenges modern organizations face is insider threats and identifying the location of malicious activity. Understanding whether documents are being improperly accessed, how users are utilizing them, and whether irregular login patterns are occurring is essential for high-value regulated content. Therefore, large organizations must know the following:
- When users access ECM applications
- Content access patterns are indicative of a security anomaly
- Content use and misuse are characteristic of insider threats Irregular document access by privileged insiders
- Suspicious login attempts from inside the firewall
- High-volume movement of content to endpoint devices
- Irregular download and upload of content
Any of the above conditions can trigger a detect, respond and contain response action. Once an event is detected, a response and contain action can be triggered depending on the severity classification. For example, for a severe event, user access can immediately be revoked, and endpoint detection and response (EDR) tools can be signaled to disable browser access and even remove an endpoint device from the network.
4. User License Management “Right-Sizing”
Understanding the number of unique users accessing your repositories is tantamount when evaluating ECM user license requirements. This is especially important during software upgrades, cloud migrations and license agreement renewals. Tracking your user counts, growth trends and users by ECM application provides a detailed context for ECM licensing conversations. This information can also feed chargeback analysis as it provides objective information on ECM usage by divisions, business areas or department user groups. Therefore, organizations need to understand this critical licensing information:
External user count by application or repository
Internal user count by application or repository
- API gateway application access using “shared” user accounts
- Native ECM application user count
- User device types such as desktop, mobile or tablet. It’s worth noting that knowing the device types aids in understanding ECM application platform preferences, investment, and DevOps process focus.
Effective user activity management within ECM systems is indispensable in today's business operations. ECM applications are at the heart of critical document processes, handling vast user interactions and document transactions daily. Being attuned to these user interactions and their usage patterns is crucial for efficient content management, enhanced user experience, and robust security protocols. It ensures smooth operations, planning for future needs, swift problem detection and resolution, securing valuable content and optimal resource allocation. Managing ECM user activity with appropriate context is vital for organizations aiming for improved security and overall operational effectiveness.
Brian DeWyer is CTO and Co-Founder of Reveille Software. With more than 25 years of experience in technology, Brian DeWyer provides product strategy and technical leadership in his role as Reveille CTO and board member. Brian leverages his extensive knowledge from his tenure as a senior IT leader at Wachovia and previous role as a process consulting practice leader for IBM Global Services delivering on-premises and cloud-based solution implementations for Fortune 1000 commercial and government clients. He has led process change efforts within large organizations, building on content-driven solutions for high-volume transaction processing applications. He is a past board member of the Association of Image and Information Management (AIIM) industry association. Brian graduated from Virginia Tech with a BSME and holds an MBA from Wake Forest University.









