
Image by: Dmitrii Kotin, ©2016 Getty Images
In business, the act of finding information we need is an everyday occurrence and the focus is heavily shifting to risk management and compliance. In fact, there was a significant shift in focus to risk and compliance in the past year.
How much of a shift?
As reported in the AIIM research report titled “Information Management – State of the Industry 2016,” in the past year, the number of large organizations citing compliance and risk as the largest driver for information management (IM) has risen from 38% to 59%. Additionally, 44% of mid-sized organizations also cite this as their biggest driver. So what’s up with that? Why this significant increase?
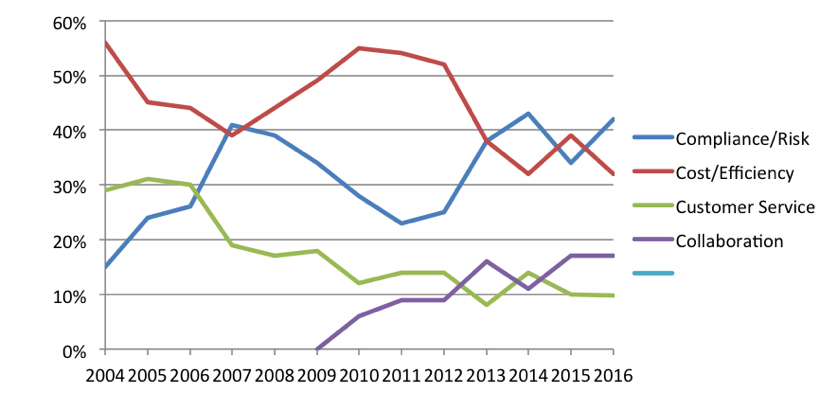
When you consider your document and records management projects, what is the most significant business driver for your organization?
Source: “Information Management – State of the Industry 2016,” AIIM 2016.
While one could cite many reasons, in my view, the underlying factor is the rise in the number of security breaches and the media attention it is given. When I talk about security breaches, I am not pointing to system hacks alone. In fact, half of the organizations we have polled feel that many of the breaches are due to employees unknowingly leaking, losing, or intentionally stealing information.
Consider this
Systems security, network security, content security, and human security should all be addressed as part of the overarching governance policy. There must be a holistic, multidimensional approach that takes into account each and every information touchpoint, access point, and repository. Compliance and risk should be a top consideration when discussing enterprise content management (ECM) and how a strong, well-planned, and well-managed information ecosystem will support compliance and risk management.
"Risk and compliance should be top of the list for all companies as a strategic initiative, not as a reactive response."
What to think about
Evaluate your current governance policies. Validate and update your current procedures, education, and supporting technologies to ensure they meet your compliance and risk requirements. Map your processes, documenting the content, touchpoints, and access points related to those processes to identify areas of vulnerability. Use these findings to develop a correction plan, establish metrics to use in monitoring progress and adherence, and implement an audit or monitoring mechanism. If you find something that needs correction, document it, correct it, and monitor again.
In my view
Risk and compliance should be top of the list for all companies as a strategic initiative, not as a reactive response. When you have to react, it is too late. Approach risk and compliance as a strategic, preventative measure to lessen the possibility of a data breach and increase the probability of detecting it, should one occur. Position your organization to be one that says, "We know about that," rather than, "What’s up with that?" when it comes to good governance practices.
Risk and compliance should be top of the list for all companies as a strategic initiative, not as a reactive response. When you have to react, it is too late. Approach risk and compliance as a strategic, preventative measure to lessen the possibility of a data breach and increase the probability of detecting it, should one occur. Position your organization to be one that says, "We know about that," rather than, "What’s up with that?" when it comes to good governance practices.
Bob Larrivee is Vice President and Chief Analyst of Market Intelligence at AIIM and an internationally recognized subject matter expert and thought leader with over 30 years of experience in the fields of information and process management. He is an avid techie with a focus on process improvement and the application of advanced technologies to enhance and automate business operations. Follow him on Twitter @BobLarrivee.
















